
Cloning system disks

Floppies have special format:
heads:2
tracks:80
sectors/track:10
sector size: 1024 bytes
Total size = 1 638 400 bytes
I used SAMdisk (https://simonowen.com/samdisk/) to read and write floppies (Windows 7 32bit) and standard 3.5″ IDE floppy drive
Remember to set original disk write protection ON before inserting to PC drive to avoid data corruption!
Read disk:
SAMdisk.exe a: hunter.dsk -s10 -z3Write disk:
SAMdisk.exe hunter.dsk a: -s10 -z3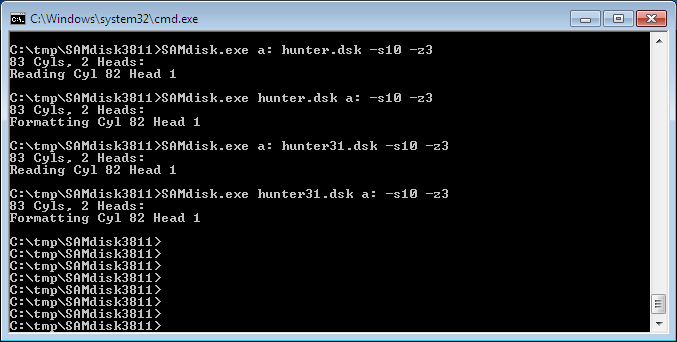
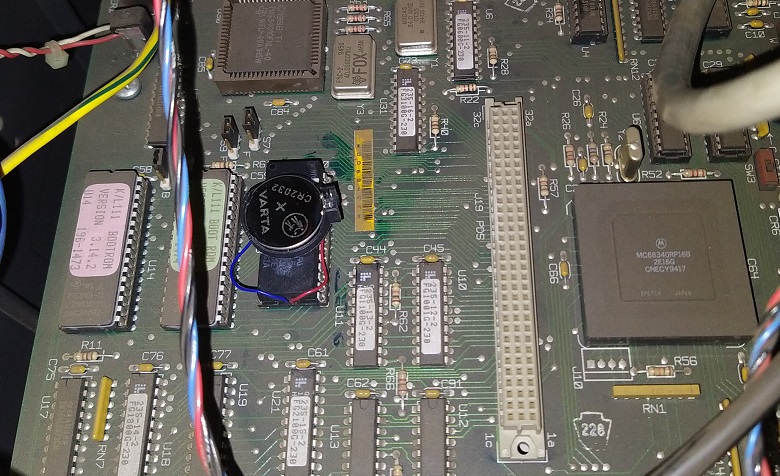
RTC Battery fix
System date and time settings were lost every time when power was switched off. There is STMicroelectronics MK48T08B-15 timekeeper ram chip on the board. That chp also have an internal battery that has gone bad during years. There is lot of instructions adding external battery for that chip. Just google ”MK48T08B-15 battery”!
Boot ROM Backup
There is two TMS27C010A EPROM (UV erasable) chips on the board. Those chips store the boot ROM SW that is executed first when power is switched on. I was little bit worried if bits start flipping around when chip aging. Manufacturer gives 10 years quarantee of stability but those are already around 30 years old.
Read binary dump files are here
Seems that those chips are addressed parallel. First 8 bits from U15 then 8 bits from U14 and again back to U15.
